Securing AI in Healthcare
A CSI Companies Solution
Unlock advanced AI solutions securely with CSI Companies. Revolutionize healthcare while protecting patient data.

CSI’s Cybersecurity Practice for
Safe AI Adoption in Healthcare
CSI’s Cybersecurity practice is focused on safely guiding healthcare organizations on their AI journey. The journey starts with the final destination in mind, which is the confidence knowing that your enterprise has the proper security measures in place for safe and responsible adoption of AI applications.
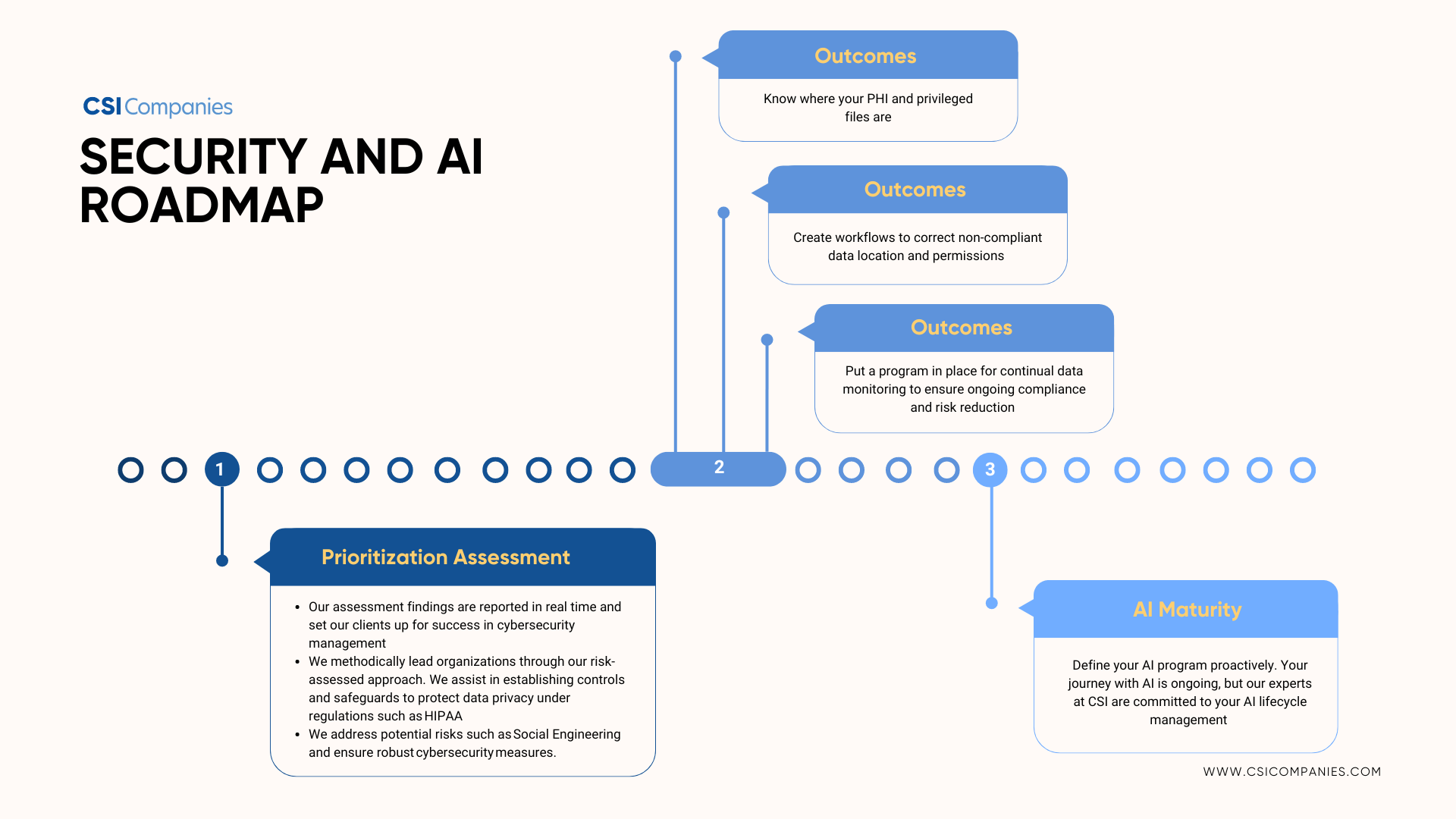
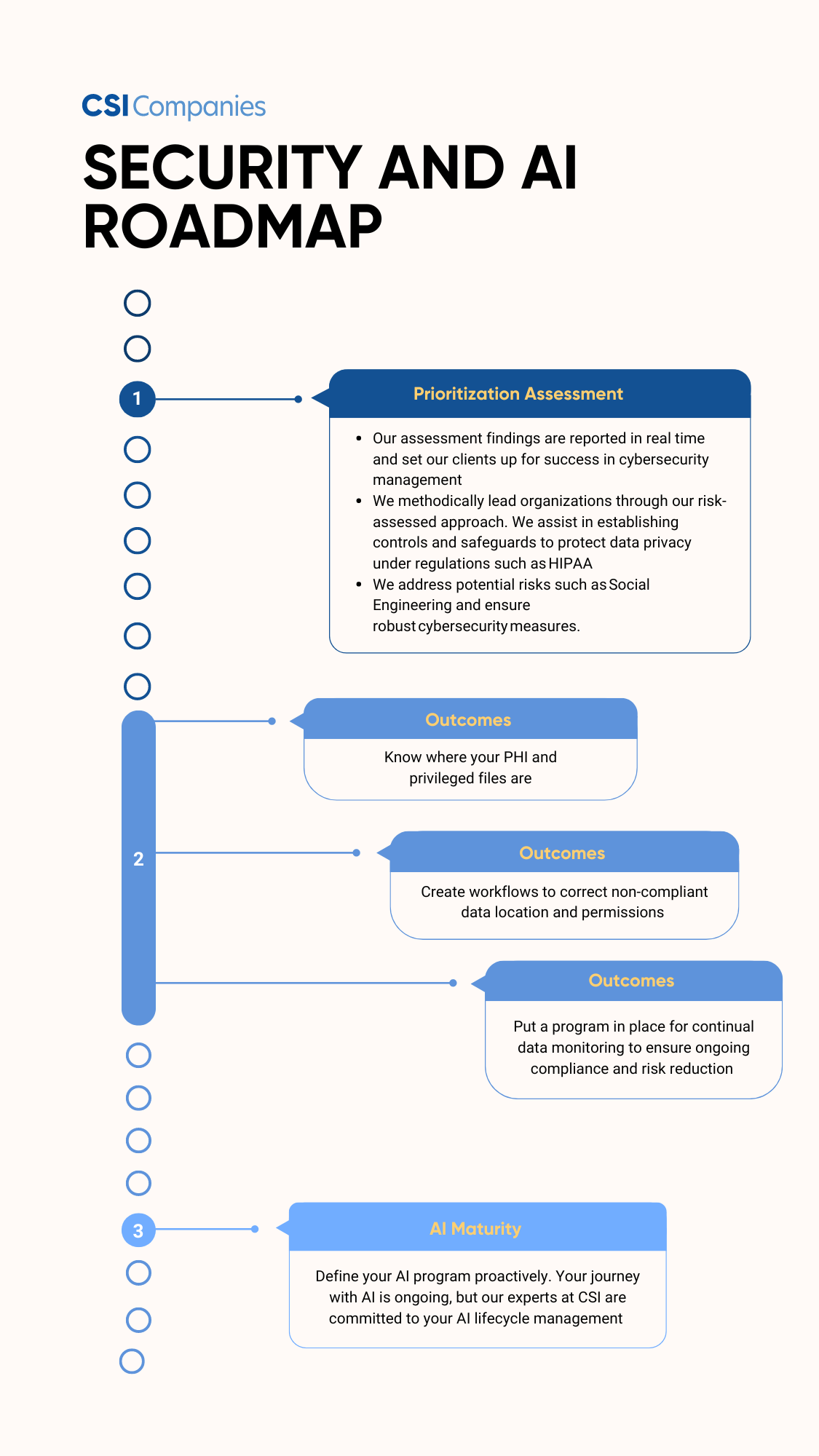
The journey starts with CSI’s AI Prioritization Roadmap which allows organizations to understand their current security posture with an emphasis on the best practice security measures to support any flavor of AI applications.
CSI’s team of veteran healthcare CTO/CISOs leads our clients through the prioritization roadmap process and creates a customized remediation plan specific to your current security posture, desired future state, and budget. During the journey, CSI will make real-time remediation suggestions categorized by high, medium, and low risks. In addition, CSI will provide guidance on adhering to the proper standards like NIST, HITRUST, and HIPAA, as well as which Cyber Security technologies should be part of your security platform to properly secure your adoption of AI today, tomorrow, and in the future
Because Cybersecurity and AI will be on-going initiatives, CSI offers multiple options to remain involved in your journey, guiding you to safe and secure AI adoption.
CSI’s Cybersecurity Practice for
Safe AI Adoption in Healthcare
CSI’s Cybersecurity practice is focused on safely guiding healthcare organizations on their AI journey. The journey starts with the final destination in mind, which is the confidence knowing that your enterprise has the proper security measures in place for safe and responsible adoption of AI applications.
The journey starts with CSI’s AI Prioritization Roadmap which allows organizations to understand their current security posture with an emphasis on the best practice security measures to support any flavor of AI applications.
CSI’s team of veteran healthcare CTO/CISOs leads our clients through the prioritization roadmap process and creates a customized remediation plan specific to your current security posture, desired future state, and budget. During the journey, CSI will make real-time remediation suggestions categorized by high, medium, and low risks. In addition, CSI will provide guidance on adhering to the proper standards like NIST, HITRUST, and HIPAA, as well as which Cyber Security technologies should be part of your security platform to properly secure your adoption of AI today, tomorrow, and in the future
Because Cybersecurity and AI will be on-going initiatives, CSI offers multiple options to remain involved in your journey, guiding you to safe and secure AI adoption.
Navigating AI Readiness with CSI: Trust, Expertise, Excellence
AI has become pervasive, permeating various aspects of our lives and industries. It is imperative to ensure that we harness the power of AI safely and effectively.
At CSI, we are equipped with industry experts, including healthcare CTOs and CISOs, to navigate you through the complexities of AI readiness.
AI readiness is a journey with a clear destination and a well-defined route to follow. This journey begins with our AI Prioritization Roadmap, where we evaluate your current standing, and culminates with the three essential components for AI integration.
Trust in CSI to lead you through this transformative journey towards AI excellence.
Navigating AI Readiness with CSI: Trust, Expertise, Excellence
AI has become pervasive, permeating various aspects of our lives and industries. It is imperative to ensure that we harness the power of AI safely and effectively.
At CSI, we are equipped with industry experts, including healthcare CTOs and CISOs, to navigate you through the complexities of AI readiness.
AI readiness is a journey with a clear destination and a well-defined route to follow. This journey begins with our AI Prioritization Roadmap, where we evaluate your current standing, and culminates with the three essential components for AI integration.
Trust in CSI to lead you through this transformative journey towards AI excellence.

To learn more about our boutique approach, talk to a CSI expert today!
AI Integration Key Phases:
1. Basic Security Measures:
Establishing a fundamental security program to safeguard sensitive data in healthcare environments.
Ensure that your cybersecurity program is aligned with industry standards in real time, covering all recommended technology areas with appropriate tools and optimal configurations. Evaluate the effectiveness of your logging and the robustness of your governance and change management program. Aim for a comprehensive view of your organization’s real-time security posture.
CSI can assist your organization in adopting and complying with NIST, HITRUST, and other security standards, paving the way for a more secure and resilient cybersecurity framework.
2. Enhanced Data Oversight:
Assisting in the evolution of data management practices with appropriate controls over accessed information. This includes permissions, access, and data classification to ensure the right people have access to only their data when adopting AI technologies.
Let’s face it, hospitals have grown their IT programs organically over the years. This leads to a proliferation of data sprawl on the network, storage platforms, end user devices, file shares, collaboration tools such as SharePoint, and so on. Getting a handle on where your sensitive data is, what the permissions are on that data (who has access), and the ability to implement workflows to correct this situation is paramount prior to adopting AI.
CSI, through our efforts, and with partners, provide a free assessment to identify your sensitive data landscape and your risk in this area. This is a key activity prior to implementing AI, especially enterprise AI applications.
3. Implementation of Guardrails for AI Adoption:
Facilitating the establishment of guidelines and protocols for seamless integration and ongoing management of AI technologies.
At CSI, we look at the adoption of AI like any other application. It’s a technology in need of lifecycle management. AI needs vendor vetting/selection, implementation, monitoring, updating, patching, and ongoing care and feeding. Adopting AI is a program and should be well defined with documented policies and procedures.
CSI Companies
Other Related Services
EHR Cloud Journeys
Organizational Change Management
Application Security Management
SOC Services
Operational and Organizational Readiness Programs
Discover why CSI Companies is the industry's leading choice for operational improvements.
CSI Insights
CSI Insights
Securing AI
Find out more about CSI's expert leading this transformation in healthcare organizations in our press release.